PROXIMANOVA-LIGHT.OTF PROXIMANOVA-LIGHTIT.OTF PROXIMANOVA-EXTRABLD.OTF PROXIMANOVA-BOLD.OTFPROXIMANOVA-BLACK.OTF
Get this font in here!
This Article Applies to:
- AVG Business Cloud Console
By default, most threats detected on the devices in your network are automatically sent to Quarantine. Via your Cloud Console, you can remotely review and either restore or delete any quarantined file. In case of a false positive detection, you can also send us the related file for analysis or exclude it from future Antivirus scans.
In the event a detected threat cannot be quarantined/deleted, running a boot-time scan should resolve the issue.
Managing Quarantined Files
To restore or delete one or more quarantined files:
- Go to the Devices page
- Click the device on which the threat was detected to open its Detail drawer
- Go to AV threats > Quarantined to access the device's Quarantine
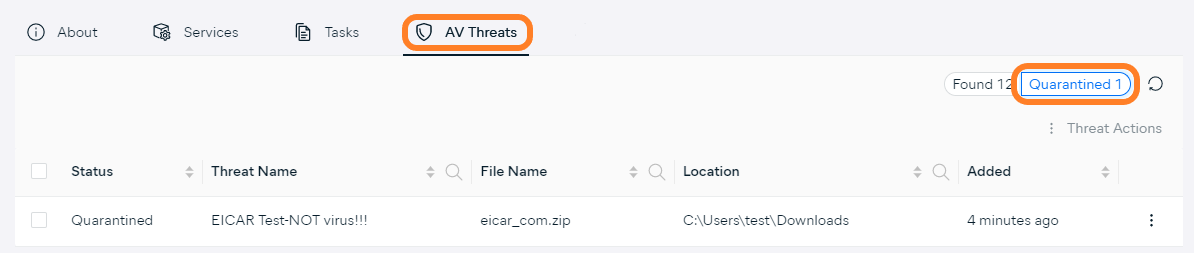
- Do one of the following:
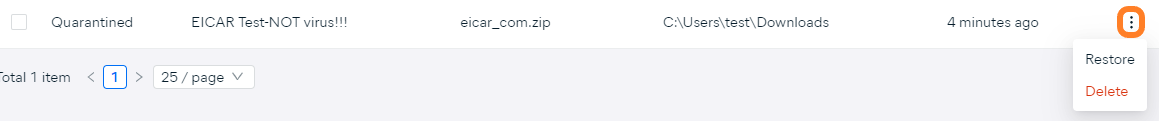
- In case of a single file, click the three dots next to the file to open its actions menu
- In case of multiple files, tick the checkboxes next to them, then click Threat Actions in the top right corner
- From the drop-down menu, select the desired action:
- Restore: Restores the file to its original location on the device. Note that this action can pose a high security risk and is only intended for specific situations (for example, if a critical system file is accidentally moved to Quarantine).
- Delete: Deletes the file from the device. Note that this action is irreversible - the file will be permanently deleted.
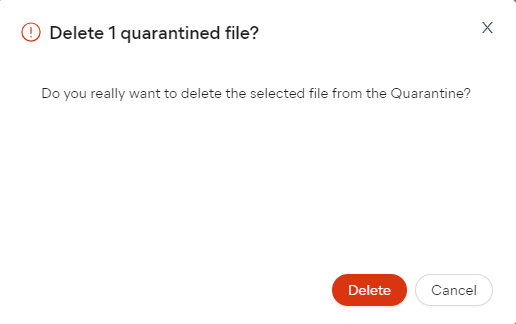
- In the confirmation prompt, click Restore/Delete
Managing False Positives
If you believe AVG Business Antivirus is falsely detecting a file as malicious, we recommend sending the file to us for further analysis (see Submitting Suspected False Positives). If our Threat Labs specialists confirm a false positive, updating virus definitions should resolve the issue.
Alternatively, you can add the file to your policy's Antivirus exclusions (see Configuring Antivirus Exclusions). Note, however, that this should be done only when you are certain that the file cannot harm your devices.
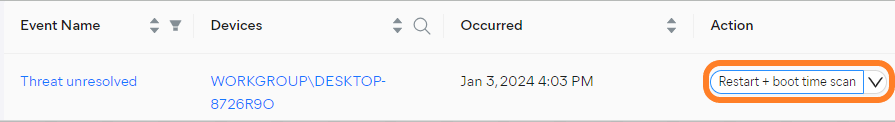
Managing Unresolved Threats
When a detected threat could not be moved to Quarantine or deleted, running a boot-time scan should resolve the issue. This can be done straight from the threat alert's actions menu (see Managing Alerts for more information).
If the issue persists, try inspecting the infected file manually (advanced users only) or reach out to AVG Business Support.
Other Articles In This Section:
Related Articles: